As the adoption of multi-factor authentication (MFA) continues to grow, phishers are turning to more sophisticated solutions (especially reverse proxy tools) to continue their attacks, it has been discovered.

Multifactor authentication (MFA) has been around since 1986, when the first RSA tokens were introduced, but it has recently become more widely used for consumer use.Duo, a provider of MFA digital authentication systems, has According to its annual State of the Auth Report, 78% of respondents will be using two/multi-factor authentication (2FA/MFA) by 2021, compared to just 28% in 2017. While many companies like Duo and RSA have made MFA more ubiquitous and user-friendly, attackers are still looking for ways to target MFA or bypass it with evolved phishing kits.
The COVID-19 pandemic has changed the way people work, and has proven that it is possible, and in some cases very effective, to work from home
This has increased security risks for companies, many of which have been mitigated by using MFA to protect employee accounts.
Even Google Inc. has recently decided to implement two-factor authentication (2FA) for all Google accounts through a step-by-step automated registration process.
MFA requires the user to provide a second authentication factor, separate from the password, to access the account. This authentication factor can be a one-time code sent via SMS or email, a token, or a unique encryption key.
This additional step is problematic for phishing attackers because the attack is not based on just stealing account credentials.
Evolution of Attack
With the proliferation of MFA, phishing attackers are turning to transparent reverse proxy solutions, and to cover this growing demand, reverse proxy-based phishing kits are being offered.
A reverse proxy is a server that sits between an Internet user and a web server behind a firewall. A reverse proxy forwards a visitor’s request to the appropriate server and sends back the resulting response.
This allows the web server to serve requests without making itself directly available on the Internet.
A report released by Proofpoint comments on a new phishing tool that provides a template for creating login web pages that mimic popular sites.
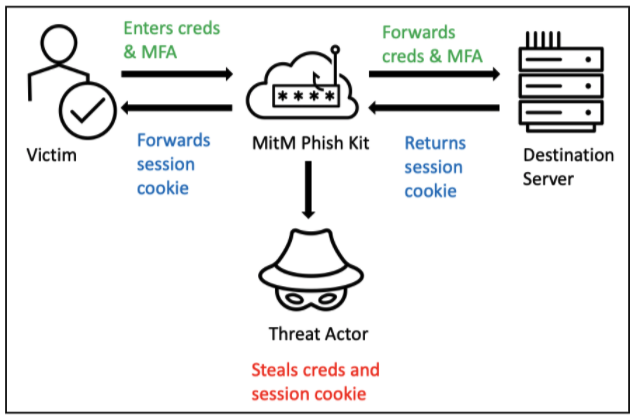
These new tools integrate the MFA snatch system, which allows attackers to steal login credentials and MFA codes that normally protect accounts.
When the victim logs into the phishing page, the tool sends the MFA to the real online service, intercepts the session cookie, and optionally forwards it to the victim.
This allows the victim to log in to the actual site and not be exposed to the attack. In the meantime, both the credentials and the cookies needed to access the account are stolen by the attacker.
Proofpoint has identified three different phishing tools that use reverse proxy systems: one using Modlishka, one using Muraena/Decrobrowser, and one using Evilginx2.
Modlishka can harvest the victim’s session even when a push notification system is employed.
Necrobrowser will be released in 2019, offering additional features such as auto-login, password change, disabling Google Workspace notifications, email dumping, SSH session key changes, and downloading repositories from GitHub.
Evilginx2 relies on a proprietary system of configurable “fishlets” that allow attackers to target any site they want. The tool also comes with several pre-installed “fishlets” that you can start using right away.
Security Blind Spot
The existence of these tools and their impact is well known, but the problem is not solved and as more phishing attackers use these tools, MFA will become less secure.
One way to deal with this problem is to identify the man-in-the-middle pages used in these attacks. However, according to a recent study, only about half of them are always on the block list.
The effectiveness of the blocklist is reduced because the domains and IP addresses used in reverse proxy attacks are constantly being updated. We have found that most of them are updated between 24 and 72 hours.
So, the only way to address this issue would be to add client-side TLS fingerprinting to help identify and filter MITM requests.



Comments