A new ransomware extortion ring called “N3TW0RM” has reportedly been carrying out cyber attacks targeting Israeli companies since early May 2021.
Israeli media Haaretz reported that at least four Israeli companies and one non-profit organization were successfully breached in this attack.
Like another ransomware extortion ring, N3TW0RM has created a data leak site and is blackmailing people into publishing their stolen files as a means of getting them to pay the ransom.
Information on two Israeli companies, H&M Israel and Veritas Logistic, has already been posted on the ransomware gang’s data leak site, and the data allegedly stolen from Veritas has already been made public.
But the ransomware extortionist has not made a high ransom demand compared to other victim companies, and Israeli media Haaretz reported that Veritas’ ransom demand was 3 Bitcoins (about $173,000: 17.3 million yen).
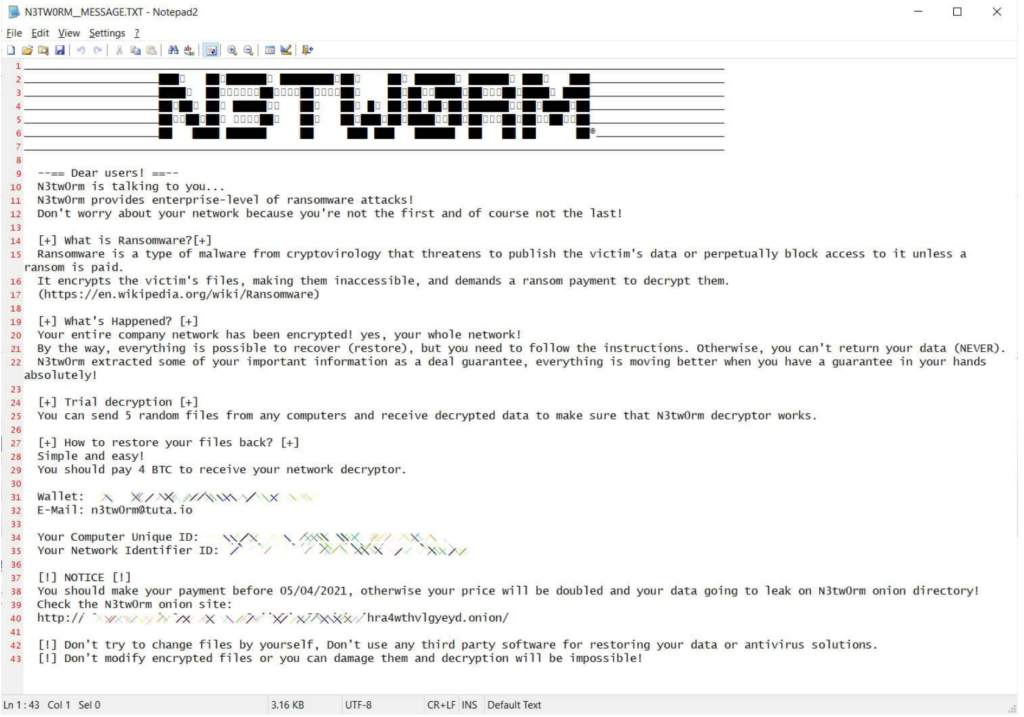
Also, a WhatsApp message shared among cybesrecurity researchers in Israel states that the ransomware “N3TW0RM” is similar in some characteristics to the Pay2Key attacks of November 2020 and February 2021.
Pay2Key, allegedly associated with an Iranian nation-state hacking group known as Fox Kitten, says its goal is to disrupt and damage Israeli interests rather than generate ransom payments.
Since the ransom demand for this ransom extortion is low and the criminal organization is not willing to negotiate, N3TW0RM has stated that they believe the attack is aimed at disrupting Israel like other organizations.
Unusual Client-Server Encryption
When encrypting data in a ransom extortion attack, criminal organizations usually attack by distributing a single type of ransomware executable to all the devices they want to encrypt.
But N3TW0RM is taking a slightly different approach this time, using a client-server model.
N3TW0RM installs a program on the victim’s server that listens for connections from client terminals.
Criminal organizations use PAExec to extract and execute the “slave.exe” client executable on all devices that the ransomware encrypts. When the file is encrypted, the file name is appended with the “.n3tw0rm” extension.
The server component would store the encryption key in a file and then instruct the client to start encrypting the device.
The advantage in this method is that there is no need to communicate to a remote command and control server (C&C server), and the ransomware operation can be completed within the victim’s network.
However, this method may not delete all the files on the server after the attack, otherwise the victim may be able to recover the data using the key on the server.




Comments