The Emotet malware is said to be the most widely spread malware in the past, using spam attacks and malicious attachments to distribute its malware.
Emotet then uses the infected device to launch other spam attacks and install other payloads such as QakBot (Qbot) and Trickbot malware. These payloads are then used for initial access to attackers to deploy ransomware such as Ryuk, Conti, ProLock, and Egregor.
In early 2021, an international law enforcement operation coordinated by Europol and Eurojust resulted in the seizure of Emotet’s infrastructure and the arrest of two people.
German law enforcement agencies used this infrastructure to deliver an Emotet module that uninstalled the malware from infected devices on April 25, 2021.
Emotet Resurrected After Law Enforcement Takedown
Researchers at Cryptolaemus, GData, and Advanced Intel have begun to see the TrickBot malware downloading a loader for Emotet onto infected devices.
Traditionally, Emotet installed TrickBot, but now attackers are using a method called “Operation Reacharound” to rebuild the Emotet botnet using TrickBot’s existing infrastructure.
Joseph Roosen, an expert on Emotet and a researcher at Cryptolaemus, said he has seen no evidence of spamming activity by the Emotet botnet and has not found any malicious documents that dropped malware.
This lack of spam activity is likely due to the fact that we are rebuilding Emotet’s infrastructure from the ground up and stealing new reply chain emails from victims in future spam attacks.
Cryptolaemus, the Emotet research group, has begun analyzing the new Emotet loader and says it contains new changes compared to previous variants.
So far, we can confirm that the command buffer has been changed. There are now 7 commands instead of 3-4
It looks like there are various execution options for the downloaded binary (since it’s not just dlls)
Vitali Kremez of Advanced Intel also analyzed the new Emotet dropper and warned that the re-emergence of malware botnets will result in a surge in ransomware infections.
We believe this is a sign of potential Emotet malware activity to facilitate large-scale ransomware operations globally, given the lack of a commodity loader ecosystem.
It also tells us that the Emotet takedown did not prevent adversaries from obtaining the malware builder and setting up a backend system to revive it
The current compilation timestamp for the Emotet loader DLL is “6191769A (Sun Nov 14 20:50:34 2021)”.
Protecting against the new Emotet botnet
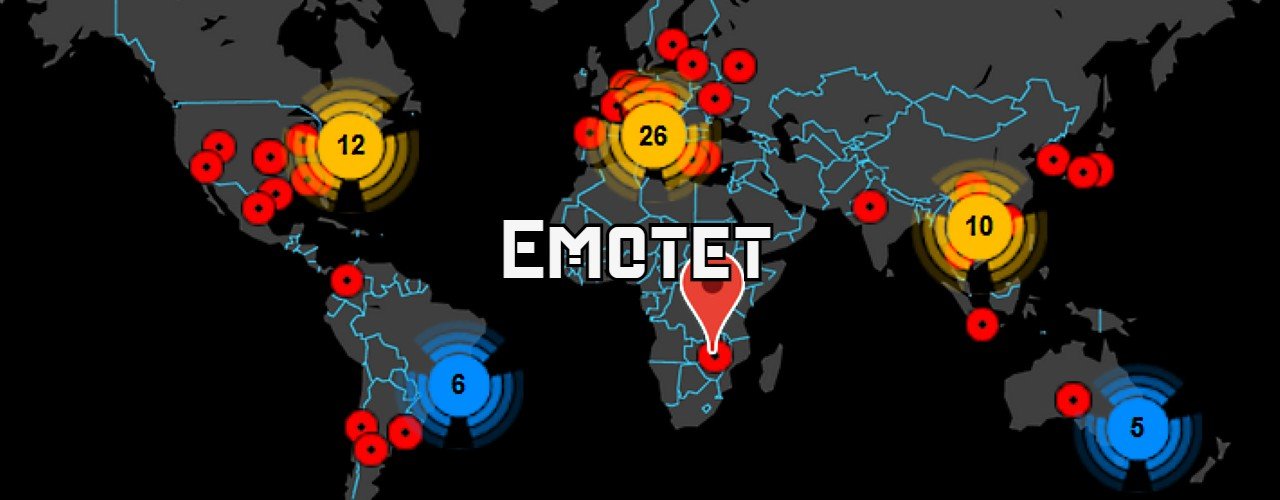
Abuse.ch, a non-profit organization that tracks malware, has published a list of command and control servers used by the new Emotet botnet and strongly recommends that network administrators block the associated IP addresses.
Unfortunately, the new Emotet infrastructure is expanding rapidly, with over 246 infected devices already acting as command and control servers.
It is highly recommended that network administrators block all relevant IP addresses to prevent their devices from being recruited into the newly reborn Emotet botnet.
https:// feodotracker.abuse.ch/downloads/ipblocklist_recommended.txt
Comments