
Match Group, the owner of multiple popular online dating services, Tinder, Match.com, Meetic, OkCupid, and Hinge, confirmed a cybersecurity incident that compromised user data.
The company stated that hackers stole a “limited amount of user data” after the ShinyHunters threat group leaked 1.7 GB of compressed files allegedly containing 10 million records of Hinge, Match, and OkCupid user information, as well as internal documents.
In a statement to , a spokesperson for Match Group confirmed the incident.
“We are aware of claims being made online related to a recently identified security incident,” the company spokesperson said.
“Match Group takes the safety and security of our users seriously and acted quickly to terminate the unauthorized access.”
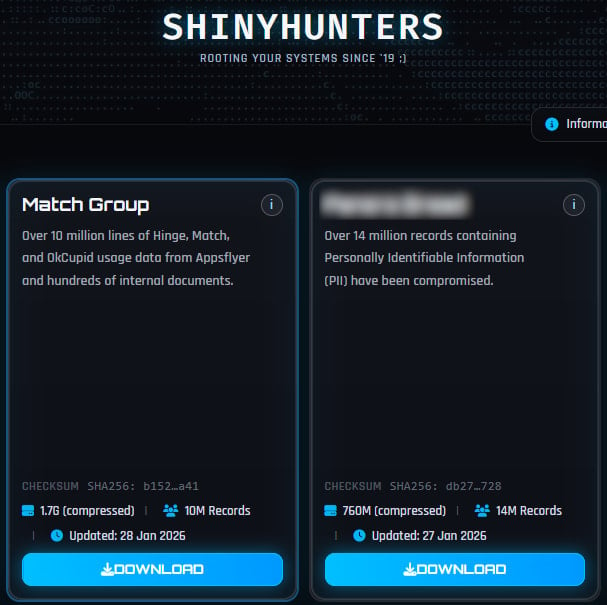
Source:
The company said the investigation into the incident is in progress with the help of external experts, and that there is no indication that the hackers accessed user log-in credentials, financial information, or private communications.
“We believe the incident affects a limited amount of user data, and we are already in the process of notifying individuals, as appropriate,” Match Group says.
Match Group is a giant in online dating, generating annual revenue of $3.5 billion, and the active user base across all its apps is estimated to be more than 80 million.
This latest incident is part of a new ShinyHunters voice phishing (vishing) campaign targeting single sign-on (SSO) accounts at Okta, Microsoft, and Google across over a hundred high-value organizations, using links to supposedly internal login portals.
In the case of Match Group, was told that the attacker stole data after compromising an Okta SSO account that gave them access to the company’s AppsFlyer marketing analytics instance and Google Drive and Dropbox cloud storage accounts.
However, the company disputed some of these claims in statement for . A Match Group spokesperson said that “based on our investigation Google Drive and Dropbox files were not accessed.”
has learned that the social engineering attack used the phishing domain at ‘matchinternal.com.’
The hackers said that the data contains personally identifiable information (PII), but not a lot of it. and that most of it consists of tracking information.
Companies can add defenses against attacks based on social-engineering by implementing solutions that are resistant to phishing attempts.
“While this is not the result of a security vulnerability in vendors’ products or infrastructure, we strongly recommend moving toward phishing-resistant MFA, such as FIDO2 security keys or passkeys where possible, as these protections are resistant to social engineering attacks in ways that push-based or SMS authentication are not,” Charles Carmakal, Mandiant’s Chief Technology Officer, says.
Furthermore, “administrators should also implement strict app authorization policies and monitor logs for anomalous API activity or unauthorized device enrollments.”
In a post last week, Okta also recommends phishing resistance to prevent access to resources.”When using Okta for workforce authentication, that would equate to enrolling users in Okta FastPass, passkeys or both for the sake of redundancy,” says Moussa Diallo, threat researcher at Okta Threat Intelligence.
“Social engineering actors can also be frustrated by setting network zones or tenant access control lists that deny access via the anonymizing services favoured by threat actors. The key is to know where your legitimate requests come from, and allowlist those networks,” Diallo said.
The researcher notes that there are some financial institutions, like Monzo Bank and the Crypto exchange, currently testing live caller checks, where users can verify in the official mobile app from the company if an authorized representative is on the phone with them.
Update [January 31st]: Article updated with statement from Match Group disputing that the threat actor accessed Google Drive and Dropbox storages during the attack.
.ia_ad {
background-color: #f0f6ff;
width: 95%;
max-width: 800px;
margin: 15px auto;
border-radius: 8px;
border: 1px solid #d6ddee;
display: flex;
align-items: stretch;
padding: 0;
overflow: hidden;
}
.ia_lef {
flex: 1;
max-width: 200px;
height: auto;
display: flex;
align-items: stretch;
}
.ia_lef a {
display: flex;
width: 100%;
height: 100%;
}
.ia_lef a img {
width: 100%;
height: 100%;
border-radius: 8px 0 0 8px;
margin: 0;
display: block;
}
.ia_rig {
flex: 2;
padding: 10px;
display: flex;
flex-direction: column;
justify-content: center;
}
.ia_rig h2 {
font-size: 17px !important;
font-weight: 700;
color: #333;
line-height: 1.4;
font-family: Georgia, “Times New Roman”, Times, serif;
margin: 0 0 14px 0;
}
.ia_rig p {
font-weight: bold;
font-size: 14px;
margin: 0 0 clamp(6px, 2vw, 14px) 0;
}
.ia_button {
background-color: #FFF;
border: 1px solid #3b59aa;
color: black;
text-align: center;
text-decoration: none;
border-radius: 8px;
display: inline-block;
font-size: 16px;
font-weight: bold;
cursor: pointer;
padding: 10px 20px;
width: fit-content;
}
.ia_button a {
text-decoration: none;
color: inherit;
display: block;
}
@media (max-width: 600px) {
.ia_ad {
flex-direction: column;
align-items: center;
}
.ia_lef {
max-width: 100%;
}
.ia_lef a img {
border-radius: 8px 8px 0 0;
}
.ia_rig {
padding: 15px;
width: 100%;
}
.ia_button {
width: 100%;
margin: 0px auto;
}
}
The future of IT infrastructure is here
Modern IT infrastructure moves faster than manual workflows can handle.
In this new Tines guide, learn how your team can reduce hidden manual delays, improve reliability through automated response, and build and scale intelligent workflows on top of tools you already use.





Comments