
The RondoDox botnet malware is now exploiting a critical remote code execution (RCE) flaw in XWiki Platform tracked as CVE-2025-24893.
On October 30, the U.S. Cybersecurity and Information Security Agency (CISA) marked the flaw as actively exploited.
Now, a report from vulnerability intelligence company VulnCheck notes that CVE-2025-24893 is being leveraged in attacks by multiple threat actors, including botnet operators like RondoDox and cryptocurrency miners.
RondoDox is a large-scale botnet malware first documented by Fortinet in July 2025 as an emerging threat. In early October, Trend Micro warned about RondoDox’s exponential growth, with recent variants targeting at least 30 devices via 56 known vulnerabilities, some of them disclosed at Pwn2Own hacking competitions.
Starting November 3, VulnCheck observed RondoDox exploiting CVE-2025-24893 through a specially crafted HTTP GET request that injected base64-encoded Groovy code through the XWiki SolrSearch endpoint, causing the server to download and execute a remote shell payload.
The downloaded script (rondo.<value>.sh) is a first-stage downloader that retrieves and executes the main RondoDox payload.
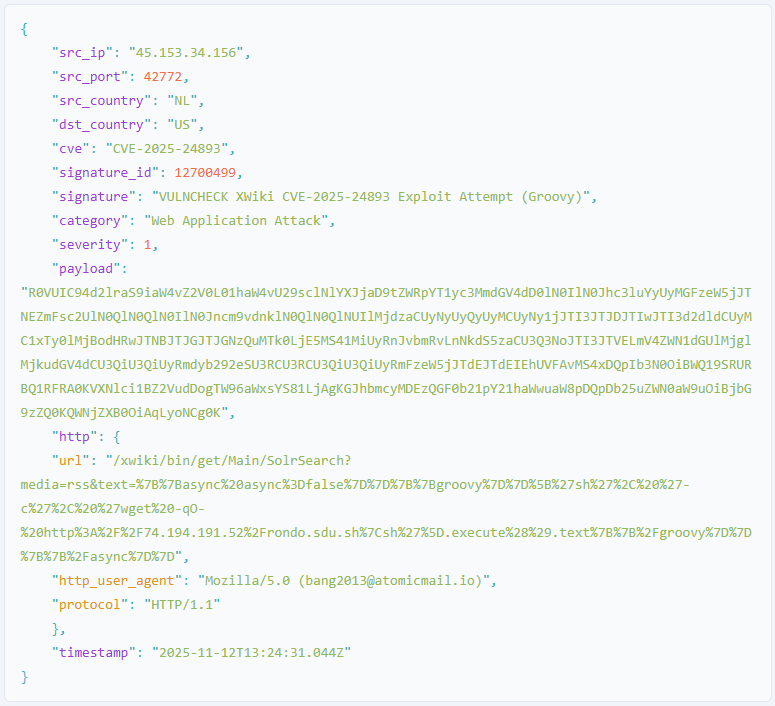
Source: VulnCheck
The researchers observed additional attacks involving cryptocurrency miner deployments on November 7, and also attempts to establish a bash reverse shell occurred on October 31 and November 11.
VulnCheck has also recorded widespread scanning using Nuclei, sending payloads that attempt to execute cat /etc/passwd via Groovy injection in the XWiki SolrSearch endpoint, as well as OAST-based probing.
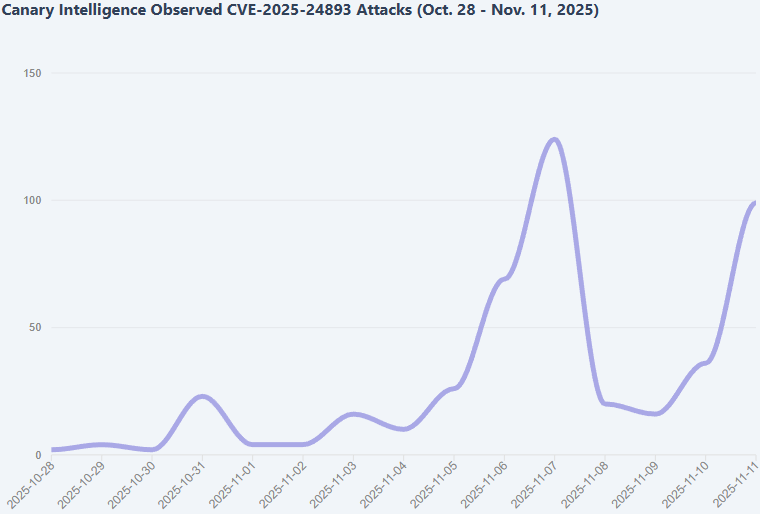
Source: VulnCheck
The XWiki Platform is a Java-based, open-source enterprise wiki platform used primarily for self-hosted internal knowledge management solutions.
CVE-2025-24893 impacts versions before 15.10.11 and 16.4.1, which are the upgrade targets for administrators. Given the active exploitation status for this flaw, immediate patching is advised.
According to the researchers, multiple attackers started to leverage the vulnerability just days after initial exploitation started.
They note that the incidents they observed come from a user-agent and documented payload servers associated with RondoDox. This means that publicly available indicators of compromise (IoCs) for the botnet should block these exploitation attempts.
.ia_ad {
background-color: #f0f6ff;
width: 95%;
max-width: 800px;
margin: 15px auto;
border-radius: 8px;
border: 1px solid #d6ddee;
display: flex;
align-items: stretch;
padding: 0;
overflow: hidden;
}
.ia_lef {
flex: 1;
max-width: 200px;
height: auto;
display: flex;
align-items: stretch;
}
.ia_lef a {
display: flex;
width: 100%;
height: 100%;
}
.ia_lef a img {
width: 100%;
height: 100%;
border-radius: 8px 0 0 8px;
margin: 0;
display: block;
}
.ia_rig {
flex: 2;
padding: 10px;
display: flex;
flex-direction: column;
justify-content: center;
}
.ia_rig h2 {
font-size: 17px !important;
font-weight: 700;
color: #333;
line-height: 1.4;
font-family: Georgia, “Times New Roman”, Times, serif;
margin: 0 0 14px 0;
}
.ia_rig p {
font-weight: bold;
font-size: 14px;
margin: 0 0 clamp(6px, 2vw, 14px) 0;
}
.ia_button {
background-color: #FFF;
border: 1px solid #3b59aa;
color: black;
text-align: center;
text-decoration: none;
border-radius: 8px;
display: inline-block;
font-size: 16px;
font-weight: bold;
cursor: pointer;
padding: 10px 20px;
width: fit-content;
}
.ia_button a {
text-decoration: none;
color: inherit;
display: block;
}
@media (max-width: 600px) {
.ia_ad {
flex-direction: column;
align-items: center;
}
.ia_lef {
max-width: 100%;
}
.ia_lef a img {
border-radius: 8px 8px 0 0;
}
.ia_rig {
padding: 15px;
width: 100%;
}
.ia_button {
width: 100%;
margin: 0px auto;
}
}
7 Security Best Practices for MCP
As MCP (Model Context Protocol) becomes the standard for connecting LLMs to tools and data, security teams are moving fast to keep these new services safe.
This free cheat sheet outlines 7 best practices you can start using today.






Comments