
Mandiant and Google are tracking a new extortion campaign where executives at multiple companies received emails claiming that sensitive data was stolen from their Oracle E-Business Suite systems.
According to Genevieve Stark, Head of Cybercrime and Information Operations Intelligence Analysis at GTIG, the campaign began in late September.
“This activity began on or before September 29, 2025, but Mandiant’s experts are still in the early stages of multiple investigations, and have not yet substantiated the claims made by this group,” Stark said.
Charles Carmakal, CTO of Mandiant – Google Cloud, stated that the extortion emails are being sent from a large number of compromised email accounts.
“We are currently observing a high-volume email campaign being launched from hundreds of compromised accounts and our initial analysis confirms that at least one of these accounts has been previously associated with activity from FIN11, a long-running financially motivated threat group known for deploying ransomware and engaging in extortion,” Carmakal explained.
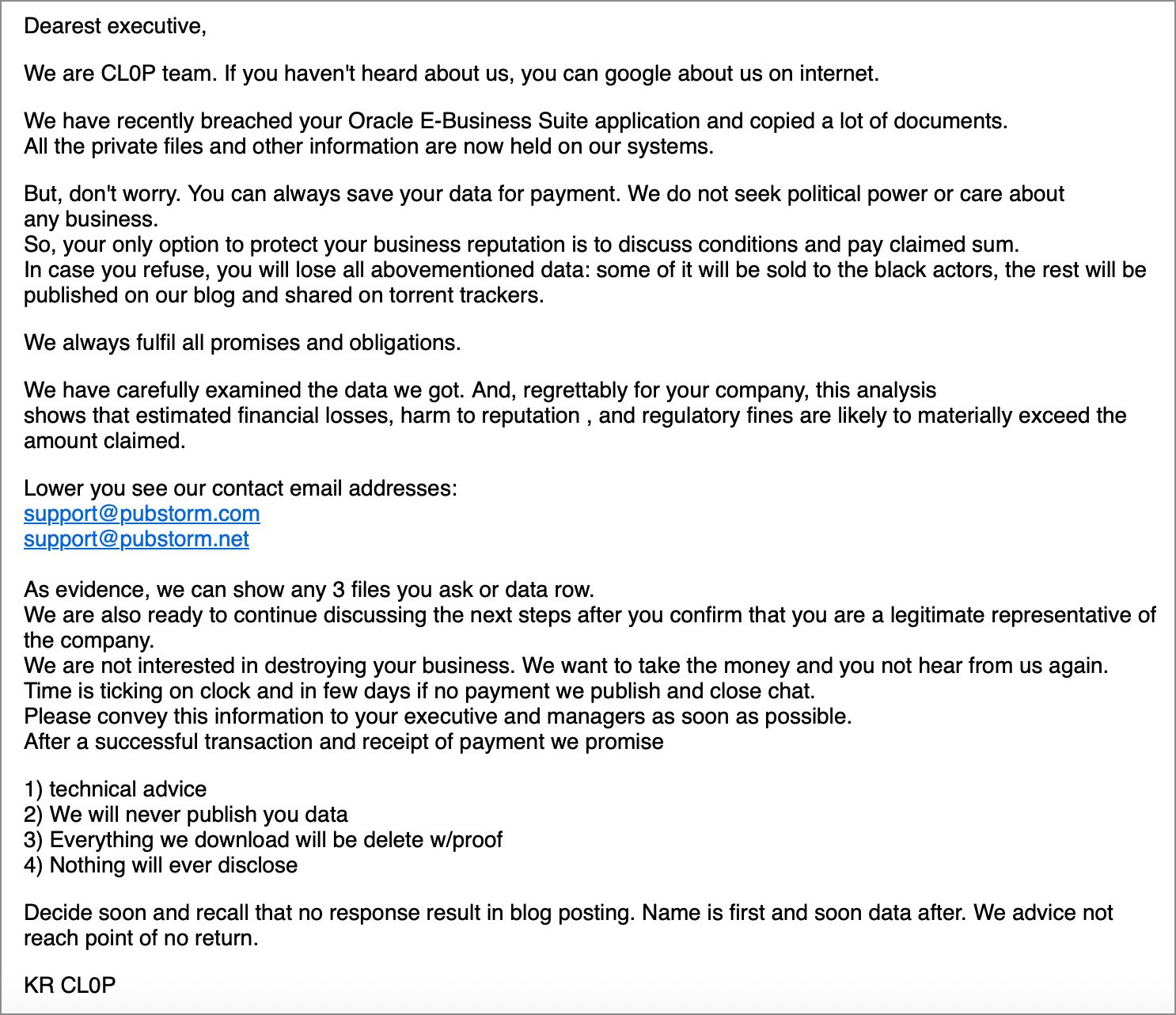
In an example of the extortion email shared with , Clop says they breached the company’s Oracle E-Business Suite in a data theft attack.
“We are CL0P team. If you haven’t heard about us, you can google about us on internet,” reads the extortion email shared with .
“We have recently breached your Oracle E-Business Suite application and copied a lot of documents. All the private files and other information are now held on our systems.”
“But, don’t worry. You can always save your data for payment. We do not seek political power or care about any business. So, your only option to protect your business reputation is to discuss conditions and pay claimed sum.”
“In case you refuse, you will lose all abovementioned data: some of it will be sold to the black actors, the rest will be published on our blog and shared on torrent trackers.”
Source: Google
Mandiant and GTIG report, and has confirmed, that the email addresses listed in the extortion email are the same as those on the Clop ransomware gang’s data leak site, indicating a possible link to the extortion group.
However, Carmakal says that while the tactics are similar to Clop’s previous extortion campaigns and the email addresses indicate a potential link, there is not enough evidence to determine if data has actually been stolen.
Mandiant and GTIG recommend that organizations receiving these emails investigate their environments for unusual access or compromise in their Oracle E-Business Suite platforms.
After publishing this story, Clop claimed to that they are involved in the extortion email, indicating a bug in Oracle’s product was exploited in the attacks. However, the threat actors would not share more detailed information about the alleged attacks.
“We not prepared to discuss details at this time,” Clop told .
“Soon all will become obvious that Oracle bugged up their core product and once again, the task is on clop to save the day. We do not damage to systems and only expect payment for services we provide to protect hundreds of biggest companies in world.”
Oracle also published a brief post today by Rob Duhart, Chief Security Officer, Oracle Security, who said that they believe the threat actors exploited vulnerabilities patched in the July 2025 security updates.
“Our ongoing investigation has found the potential use of previously identified vulnerabilities that are addressed in the July 2025 Critical Patch Update,” explained Duhart.
“Oracle reaffirms its strong recommendation that customers apply the latest Critical Patch Updates.”
If you have any information regarding this incident or any other undisclosed attacks, you can contact us confidentially via Signal at 646-961-3731 or at tips@bleepingcomputer.com.
Who is the Clop extortion gang?
The Clop ransomware operation, also tracked as TA505, Cl0p, and FIN11, launched in March 2019 when it began targeting enterprise networks with a variant of the CryptoMix ransomware.
Like other ransomware gangs, Clop members breach corporate networks, steal data, and then deploy ransomware to encrypt systems.
The stolen data and encrypted files are then used as leverage to force companies to pay a ransom demand in exchange for a decryptor and to prevent the leaking of the stolen data.
While the group is still known to deploy ransomware, since 2020, they have shifted to exploiting zero-day vulnerabilities in secure file transfer platforms to steal data.
Some of their most notable attacks include:
- 2020: Exploiting a zero-day in the Accellion FTA platform, affecting nearly 100 organizations.
- 2021: Exploiting a zero-day in SolarWinds Serv-U FTP software.
- 2023: Exploiting a zero-day in the GoAnywhere MFT platform, breaching over 100 companies.
- 2023: Exploiting a zero-day in MOVEit Transfer was Clop’s most extensive campaign to date, where a zero-day exploit allowed data theft from 2,773 organizations worldwide.
The most recent campaign associated with Clop was in October 2024, when the threat actors exploited two Cleo file transfer zero-days (CVE-2024-50623 and CVE-2024-55956) to steal data and extort companies.
The U.S. State Department currently offers a $10 million reward through its Rewards for Justice program for information linking Clop’s ransomware activities to a foreign government.
Update 10/2/25: Added sample of Clop extortion email being sent to companies.
Update 10/2/25 07:42 PM ET: Added statement from the Clop ransomware gang and further info from Oracle.
.ia_ad {
background-color: #f0f6ff;
width: 95%;
max-width: 800px;
margin: 15px auto;
border-radius: 8px;
border: 1px solid #d6ddee;
display: flex;
align-items: stretch;
padding: 0;
overflow: hidden;
}
.ia_lef {
flex: 1;
max-width: 200px;
height: auto;
display: flex;
align-items: stretch;
}
.ia_lef a {
display: flex;
width: 100%;
height: 100%;
}
.ia_lef a img {
width: 100%;
height: 100%;
object-fit: cover;
border-radius: 8px 0 0 8px;
margin: 0;
display: block;
}
.ia_rig {
flex: 2;
padding: 10px;
display: flex;
flex-direction: column;
justify-content: center;
}
.ia_rig h2 {
font-size: 17px !important;
font-weight: 700;
color: #333;
line-height: 1.4;
font-family: Georgia, “Times New Roman”, Times, serif;
margin: 0 0 14px 0;
}
.ia_rig p {
font-weight: bold;
font-size: 14px;
margin: 0 0 clamp(6px, 2vw, 14px) 0;
}
.ia_button {
background-color: #FFF;
border: 1px solid #3b59aa;
color: black;
text-align: center;
text-decoration: none;
border-radius: 8px;
display: inline-block;
font-size: 16px;
font-weight: bold;
cursor: pointer;
padding: 10px 20px;
width: fit-content;
}
.ia_button a {
text-decoration: none;
color: inherit;
display: block;
}
@media (max-width: 600px) {
.ia_ad {
flex-direction: column;
align-items: center;
}
.ia_lef {
max-width: 100%;
}
.ia_lef a img {
border-radius: 8px 8px 0 0;
}
.ia_rig {
padding: 15px;
width: 100%;
}
.ia_button {
width: 100%;
margin: 0px auto;
}
}
The Security Validation Event of the Year: The Picus BAS Summit
Join the Breach and Attack Simulation Summit and experience the future of security validation. Hear from top experts and see how AI-powered BAS is transforming breach and attack simulation.
Don’t miss the event that will shape the future of your security strategy





Comments