
Update 7/25:25: Expel researchers have recanted their story, stating that while the the threat actors are attempting to use a phishing attacks to bypass FIDO authentication, the Cross-Device Authentication flow would have failed as the attackers were not in close proximity.
The researchers explain that this would have prevented the attackers from logging in to the network.
Their full statement is below.
“The original post described a new form of phishing attack that allowed an attacker to circumvent a FIDO passkey protected login. It stated that this attacker used cross-device authentication to successfully authenticate while not in close proximity to the authenticating client device,” explains Expel.
“The evidence does show the targeted user’s credentials (username and password) being phished and that the attacker successfully passed password authentication for the targeted user. It also shows the user received a QR code from the attacker. This QR code, when scanned by a mobile device, initiates a FIDO Cross-Device Authentication flow, which according to FIDO specification requires local proximity to the device which generated the QR code (the WebAuthn client). When properly implemented, without proximity, the request will time out and fail.”
“So, at the time of the original post, Expel believed the attacker successfully completed the authentication workflow, resulting in access to protected resources. After discussing these findings with the security community, we understand that this is not accurate. The Okta logs show the password factor passing successfully, but all subsequent MFA challenges failed and the attacker is never granted access to the requested resource.”
has changed the title of the post to indicate it was just an attempt to downgrade.
Our original title was: “Threat actors try to downgrade FIDO2 MFA auth in PoisonSeed phishing attack”
The original story is below.
A PoisonSeed phishing campaign is bypassing FIDO2 security key protections by abusing the cross-device sign-in feature in WebAuthn to trick users into approving login authentication requests from fake company portals.
The PoisonSeed threat actors are known to employ large-volume phishing attacks for financial fraud. In the past, distributing emails containing crypto seed phrases used to drain cryptocurrency wallets.
In the recent phishing attack observed by Expel, the PoisonSeed threat actors do not exploit a flaw in FIDO2’s security but rather abuse the legitimate cross-device authentication feature.
Cross-device authentication is a WebAuthn feature that allows users to sign in on one device using a security key or authentication app on another device. Instead of requiring a physical connection, such as plugging in a security key, the authentication request is transmitted between devices via Bluetooth or a QR code scan.
The attack begins by directing users to a phishing site that impersonates corporate login portals, such as from Okta or Microsoft 365.
When the user enters their credentials into the portal, the campaign uses an adversary-in-the-middle (AiTM) backend to silently log in with the submitted credentials on the legitimate login portal in real-time.
The user targeted in the attack normally would use their FIDO2 security keys to verify multi-factor authentication requests. However, the phishing backend instead tells the legitimate login portal to authenticate using cross-device authentication.
This causes the legitimate portal to generate a QR code, which is transmitted back to the phishing page and displayed to the user.
When the user scans this QR code using their smartphone or authentication app, it approves the login attempt initiated by the attacker.
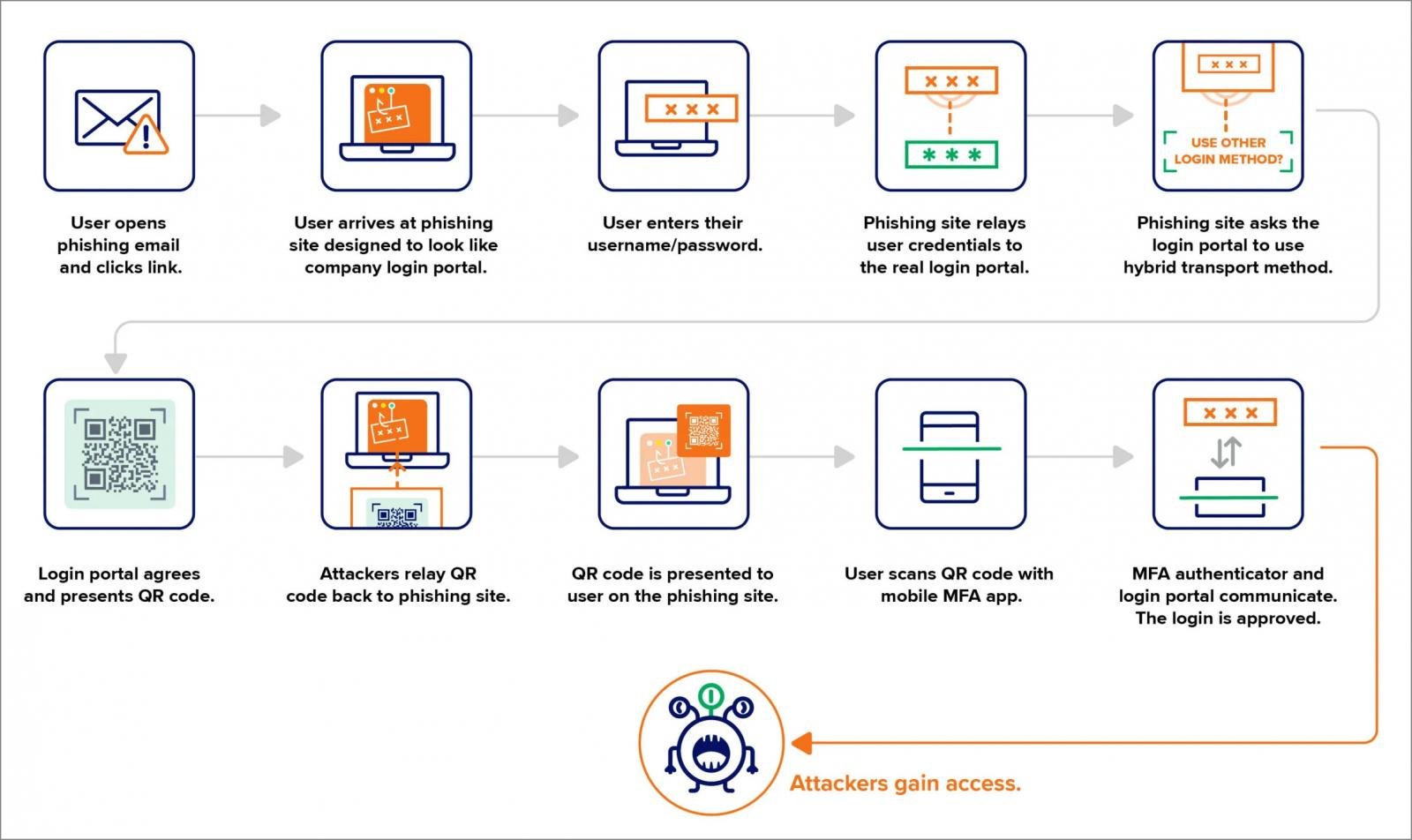
Source: Expel
This method effectively bypasses FIDO2 security key protections by allowing attackers to initiate a login flow that relies on cross-device authentication instead of the user’s physical FIDO2 key.
Expel warns that this attack does not exploit a flaw in the FIDO2 implementation, but instead abuses a legitimate feature that downgrades the FIDO key authentication process.
To mitigate the risk, Expel recommends the following defenses:
- Limiting geographic locations from which users are allowed to log in and establishing a registration process for individuals traveling.
- Routinely check for the registration of unknown FIDO keys from unknown locations and uncommon security key brands.
- Organizations can consider enforcing Bluetooth-based authentication as a requirement for cross-device authentication, which significantly reduces the effectiveness of remote phishing attacks.
Expel also observed a separate incident where a threat actor registered their own FIDO key after compromising an account via what is believed to be phishing and resetting the password. However, this attack did not require any methods to trick the user, like a QR code.
This attack highlights how threat actors are finding ways to bypass phishing-resistant authentication by tricking users into completing login flows that bypass the need for physical interaction with a security key.
.ia_ad {
background-color: #f0f6ff;
width: 95%;
max-width: 800px;
margin: 15px auto;
border-radius: 8px;
border: 1px solid #d6ddee;
display: flex;
align-items: stretch;
padding: 0;
overflow: hidden;
}
.ia_lef {
flex: 1;
max-width: 200px;
height: auto;
display: flex;
align-items: stretch;
}
.ia_lef a {
display: flex;
width: 100%;
height: 100%;
}
.ia_lef a img {
width: 100%;
height: 100%;
/*object-fit: cover;*/
border-radius: 8px 0 0 8px;
margin: 0;
display: block;
}
.ia_rig {
flex: 2;
padding: 10px;
display: flex;
flex-direction: column;
justify-content: center;
}
.ia_rig h2 {
font-size: 17px !important;
font-weight: 700;
color: #333;
line-height: 1.4;
font-family: Georgia, “Times New Roman”, Times, serif;
margin: 0 0 14px 0;
}
.ia_rig p {
font-weight: bold;
font-size: 14px;
margin: 0 0 clamp(6px, 2vw, 14px) 0;
}
.ia_button {
background-color: #FFF;
border: 1px solid #3b59aa;
color: black;
text-align: center;
text-decoration: none;
border-radius: 8px;
display: inline-block;
font-size: 16px;
font-weight: bold;
cursor: pointer;
padding: 10px 20px;
width: fit-content;
}
.ia_button a {
text-decoration: none;
color: inherit;
display: block;
}
@media (max-width: 600px) {
.ia_ad {
flex-direction: column;
align-items: center;
}
.ia_lef {
max-width: 100%;
}
.ia_lef a img {
border-radius: 8px 8px 0 0;
}
.ia_rig {
padding: 15px;
width: 100%;
}
.ia_button {
width: 100%;
margin: 0px auto;
}
}
The Board Report Deck CISOs Actually Use
CISOs know that getting board buy-in starts with a clear, strategic view of how cloud security drives business value.
This free, editable board report deck helps security leaders present risk, impact, and priorities in clear business terms. Turn security updates into meaningful conversations and faster decision-making in the boardroom.





Comments