It is commonly referred to as “DLL hijacking (DLL hijacking)”, “DLL spoofing”, “DLL preloading”, or “binary planting”.
A vulnerability in the program allows the program to execute a malicious DLL contained in the same folder as the opened data file, thinking it is a legitimate DLL, and become a victim of an attack.
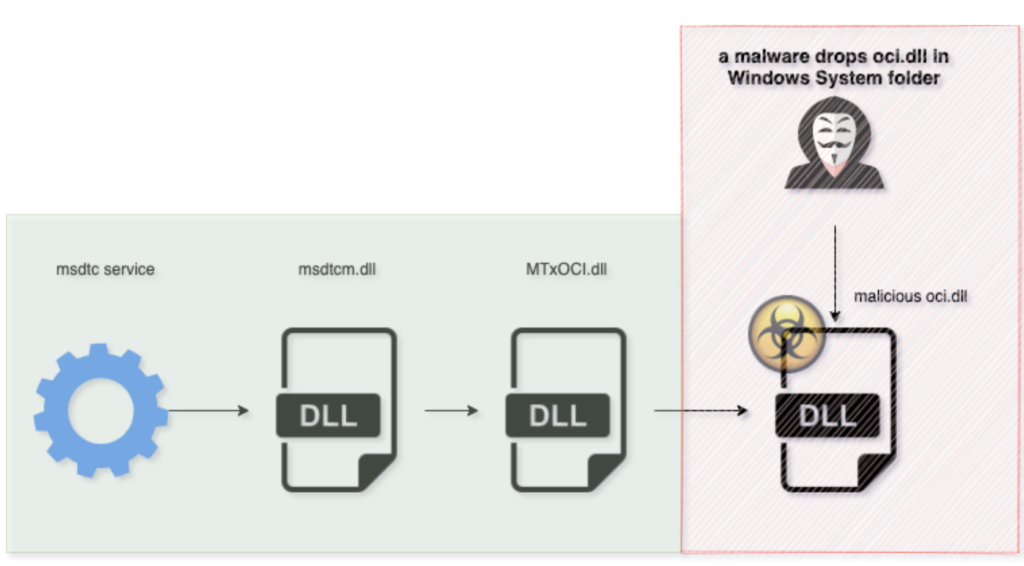
This attack was discovered in 2000 and became known worldwide as hundreds of programs were found to be vulnerable
Programs that are executed from user-writable folders such as file downloads or Temp directories are said to be affected by this vulnerability in most cases.
Example of Hijacking : New Windows Malware ‘Pingback’ Uses ICMP Appears


Comments